In the great Internet of Things gold rush, early adopters have largely left behind identity and access management. As a result, many organizations are scrambling to deal with the consequences as the IoT is vulnerable to hacks that can give malicious actors control over connected devices. Recent DDoS attacks and connected car hijackings highlight the need for greater IoT security.
Managing and securing the IoT is a critical step for organizations looking to deliver on their digital business objectives, like personalization and real-time data analysis. Successful IoT implementations build complex relationships between people, devices, and services, and the only sustainable and secure method for delivering real end user or operational value from device led solutions, is to enable persistent identity across all touchpoints. Legacy IAM is not enough. With an IoT-ready identity platform, you can securely support healthcare wearables, connected cars, or whatever yet-to-be-invented “thing” you and your customers are using now and in the years ahead.
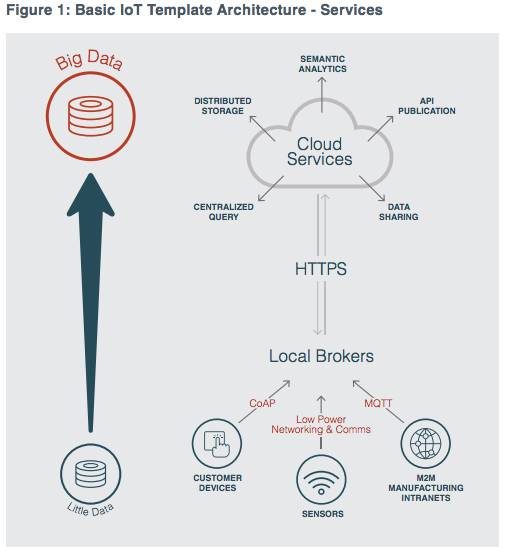
Download this overview to learn:
- Why the IoT needs identity and access management
- The basics of an IoT ready IAM solution
- How identity can support customer and industrial IoT use cases
- How to deploy a secure IoT architecture that includes identity intelligence


